Graphics by Cassandra Stephenson
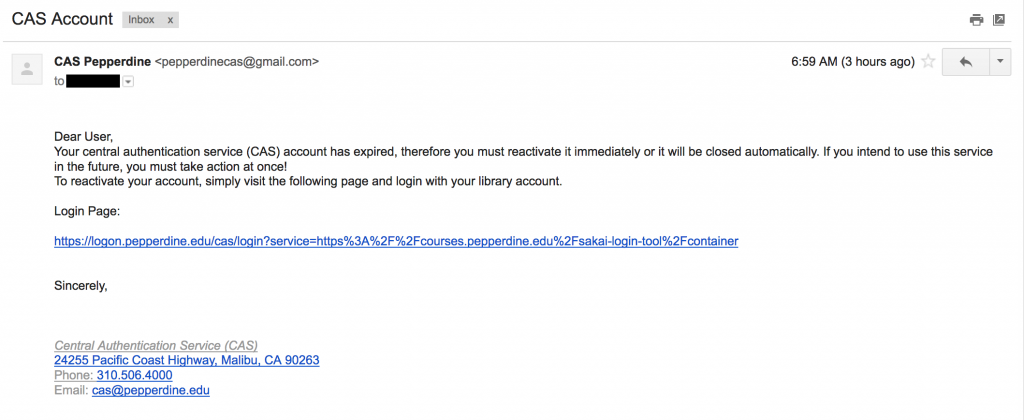
The Pepperdine Information Security Office confirmed an email sent to a Pepperdine account Feb. 8 posing as a notification from Pepperdine Central Authentication Service was in fact a fraudulent attempt to gain sensitive password information.
But according to Pepperdine Chief Information Security Officer Kim Cary, this isn’t anything new. This type of message is sent to Pepperdine accounts multiple times every year, Cary wrote in an email, and the content and style of these fraudulent emails can vary widely.
“[Phishing emails] recur regularly as phishing campaigns adjust to industry and automated defenses,” Cary wrote. “However, teaching people to delete the message if it seems suspicious and checking for a verified Pepperdine web page (using the address bar and not the graphics) before submitting their ID & Password would be very helpful.”
Phishing emails are emails that may appear to come from legitimate sources but are actually intended to trick users into giving up sensitive information, including login credentials and credit card information. These and other fraudulent or spam emails are prevalent at Pepperdine, with more than 7.8 million illegitimate email messages being processed in a five-week period by Pepperdine mail servers, according to university data.
The email received on Feb. 8 informed the recipient that their CAS “account” had expired and instructed the user to immediately reactivate it by clicking on a link and providing login information. The email included legitimate Pepperdine contact information but was sent from “pepperdinecas@gmail.com.”
Cary wrote that this type of email:
- Uses the Pepperdine name and department name in the message
- May have official Pepperdine graphics copied from web pages, including our CAS page
- May have mail addresses that spoof or imitate Pepperdine mail addresses
- Requests immediate action
- Occurs throughout each year
Information Security worker Thor Anderson wrote in an email that official communications from Pepperdine will come from accounts with “@pepperdine.edu” endings. He also noted Pepperdine does not refer to accounts as “CAS accounts” because CAS is a service they use, not something used to identify accounts.

Being aware of these elements is one skill for more safely navigating the internet, Cary wrote.
“The Information Security Office’s goal is to try to get people to develop an Internet self-defense skill where they respond to suspicious messages by either contacting the alleged sender at a published address or phone or just trust[ing] their own judgement that the message is suspicious and delet[ing] it,” Cary wrote.
________________________
Follow Cassandra Stephenson on Twitter: @CassieKay27