Graphics by Kelly Rodriguez
Pepperdine is ramping up its cybersecurity defenses as the issue of cyber attacks continues to hit close to home.
“Some of the [community] members may think, ‘Pepperdine is small, who would want to target us anyway?’” Pepperdine Chief Information Officer Jonathan See said. “Our data tells us otherwise.”
Pepperdine logged more than 2.3 million probes and attacks on Pepperdine University systems between Aug. 28 and Sept. 27, 2016, according to data collected by the university. One year later, between July 28 and Aug. 29 of 2017, Pepperdine recorded more than 5.7 million attempts to breach Pepperdine’s systems.
With this rise in attack attempts and the lessons left behind by nationwide breaches of big brands like Equifax and Target, the Pepperdine Information Security Office is continuing to fortify its protections against cyber attacks, See said. Pepperdine recently wrapped up its fourth year of championing National Cyber Security Awareness Month in October to spread awareness of cyber threats and risk and share best practices. But according to See, even Pepperdine’s multi-faceted information security program, which is regularly reviewed by the FBI Cybersecurity Task Force, is not foolproof.
“As good as your program may be, at the end we’re relying on the user,” See said. “So it has to be a shared responsibility.”
Users are the weakest link, See said, because they can unknowingly expose the system to threats by simply clicking a link or opening an email. And Pepperdine receives a lot of phishing emails — emails that attempt to trick users into giving personal information or opening malicious links or files — See said.
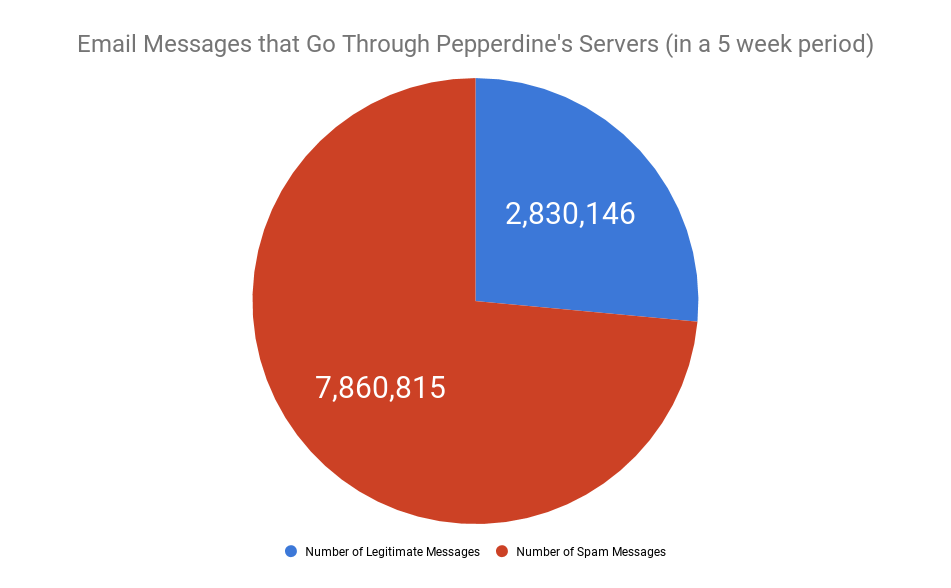
Over a five-week period this year, the Pepperdine mail servers processed nearly 11 million messages to staff and students, according to university data. Of these 11 million, just 2.8 million were considered legitimate messages. More than 6.5 million messages were “blocked connections,” or known threats. The remaining messages were spam and viruses.
See said he shared this information to spread awareness of the cyber threats that Pepperdine’s system faces. “This is common across all other institutions,” he added.
The Power of Passwords
Chief Information Security Officer Kim Cary said one goal of Pepperdine’s ISO is to inform students about best practices on the internet.
“When we’re small, our parents or guardians teach us how to cross the street, right?” Cary said. “And who has taught us how to cross the internet?”
Pepperdine ISO encourages students to use a password manager, Cary said. Most password managers are free, See said, and Pepperdine suggests students use LastPass, which they can get through the university or on their own.
The password manager acts as a database for all of an individual’s passwords that connects with browsers as a plug-in. Each time an individual logs into an online account, they sign in with one strong master password to access the plug-in application, which then provides the password for that site.
“That’s the last password that you ever know,” Cary said.
The plug-in can generate unique passwords for new and existing accounts, measure the security of existing passwords, and alert users when a certain site has been hacked or they need to change their password.
This provides stronger protection against hacking, Cary said, because if any one account gets hacked, the hackers will not be able to access any other accounts.
“There’s very few people I’ve met of any age, walk of life [and] culture that use a different password for every site,” Cary said. “Most people use the same password for every site and some people vary it slightly.”
This practice may aid in password memory but becomes problematic when a password is compromised, See said.
See said he likely has access to about 120 different sites and applications, and students likely have access to nearly as many now with more to come as they start their careers.
“I cannot remember the passwords for all of those, and I don’t want to write those passwords on a piece of paper, and that shouldn’t be the case either,” See said. “So why not adopt a password manager so that you can have a 15 [or] 18 character password, alpha-numeric, very cryptic?”
If students choose to use LastPass, Cary said it is 100 percent private and Pepperdine has no control of any of the passwords.
“It’s so private that even the company can’t get [a passphrase] back for you because they never have access to your passphrase,” he explained.
An Update a Day Keeps the Bugs Away
Pepperdine ISO also recommends students get the BrowserCheck plugin or an equivalent as another line of defense, Cary said.
“You are ahead of the game if you do one of these two things,” Cary said. “If you do both these things you are far ahead of the game.”
Just as a car needs the oil changed and tread wear monitored, computers need checkups too, he said. “Your computer has things get old,” Cary said. “It gets gummy. And you need to update them or there’s going to be a problem … it’s updates instead of oil changes.”
The BrowserCheck plugin monitors other browser plugins, the computer’s operating system and the software on computer apps to make sure they are up to date. If an update is needed, the plugin directs users to the manufacturer’s website to get the update, helping to protect against fake updates from hackers that pose as software companies.
“That’s really important because software that isn’t updated is kind of like a screen that’s got a hole in it,” Cary said. “The flies are going to come through the screen.”
And this does not apply only to computers, Cary added. For example, iPhones tend to update themselves but are still vulnerable to phishing. Cary recommended that students turn on two-factor authentication, which requires a second factor in addition to a password to unlock an account, wherever possible. This applies to Apple IDs, online banking, online gaming and music collections, to name a few, Cary said.
Simply being aware of what one clicks, even on social media sites or sites that look like they are familiar, is important as hackers become more creative, See said.
“My recommendation would be for all students to pause, think about what they’re going to click, and then connect,” he said.
Hackers can design website graphics to look like those on Wavenet, for example. If the web address does not appear as it should, it may be a fake site designed to steal your login credentials, See explained. Unexpected or odd emails and suspect links on social media can download malware, viruses or keyloggers onto the device being used.
See also recommends students back up their devices in case they are targeted by ransomware, which encrypts computers and demands a ransom to return a user’s data. If a student does think they have inadvertently clicked something, they should visit Tech Central in the Thornton Administrative Center basement in B100, See said.
Cary said that being targeted by a cyber attack is not uncommon. “You don’t even have to do anything or go to the ‘back alley’ of the internet,” he said.
“You have to understand that the people that are coming against you on the internet are there to make money off of you,” Cary said, explaining that this makes college students targets because they tend to have higher paying jobs. “If they can get into your digital life now by exploiting weaknesses in your browser or getting your password from one place and using it in your other places, then they are in position when you’re worth more to do more.”
Multiple Lines of Defense
Pepperdine has multiple layers of defense against cyber attacks that See describes as an “onion.” The first layer, a next-generation firewall, detects and bounces off nearly 6 million known threats. A local spam filter and the Google spam filter act as the second line of defense. Pepperdine ISO also does monthly maintenance on the servers, bringing them down temporarily for updates and security patches.
“Whenever we bring down a system, sometimes it creates inconvenience, but look at the downside if we don’t do this,” See said.
Pepperdine also requires faculty and staff to keep their systems updated and the system’s network access control ensures that only individuals with Pepperdine login credentials can access the system.
Any faculty and staff using virtual private networks outside of Pepperdine’s system — in a coffee shop, for instance — must now use multi factor authentication.
“The reason is that people get tricked out of their passwords,” Cary said. “People get them stolen by malware on their computers and so forth and what we don’t want is somebody to then come across the internet into our campus and wreak havoc. The multi factor authentication kind of prevents that even if the password is stolen.”
Those who do not use VPNs are not required to adopt multi-factor authentication, but See is offering those who do three years expiration on their passwords before they need to change them as opposed to the usual one.
“Even as good as we are, the user is the weakest link, because if you get phished, and you give away your credentials, it’s risky,” See said.
To train community members, Pepperdine manufactures and sends their own “phishing messages” as part of IT’s education component. Cary said this training is meant to help faculty and staff safeguard student data, and the test emails are not sent to students.
In phishing security tests sent to faculty and staff from Aug. 2016 to July 2017, the fake phishing emails received 566 clicks and 13 replies. Two individuals opened attachments on the phony emails, and 273 entered data (such as login credentials) when prompted.
In this “live-fire training,” community members receive training the moment they make a mistake, Cary said. Once an individual clicked on the email, opened the attachment or entered information, a page would appear explaining the test and what that individual should have done.
But even this type of training is not entirely effective, Cary said.
“What we find and what I’ve seen research say is even if you spend a lot of time teaching somebody how to recognize fraud in a cyber area, about six percent to 12 percent of the people will still fall for it every time,” Cary said. “And we see that happening, and it’s just better if it isn’t possible for them, at least with the things that are very valuable to us.”
See stressed that even with all of these protections and training resources, defenses will never be 100 percent effective.
“It’s high-risk now,” See said. “We just live in a very high-risk world. You can never be careful enough.”
_______________
Follow Cassandra Stephenson on Twitter: @CassieKay27
